Easy!Appointments supports LDAP (Lightweight Directory Access Protocol) authentication, allowing your staff and administrators to log in using credentials from a central directory such as Active Directory or OpenLDAP. This is especially useful for organizations that want centralized user management and single sign-on (SSO) capabilities.
LDAP is only available for staff and admin users. Customers still use the public booking form and do not require LDAP credentials.
Benefits of LDAP Integration
- Centralized account management
- Improved security and password policy enforcement
- Seamless login experience for employees
- Supports Active Directory and OpenLDAP
Prerequisites
Before enabling LDAP authentication:
- You must have an operational LDAP server (e.g., Microsoft Active Directory).
- Easy!Appointments must be able to connect to the server (network/firewall access).
- LDAP credentials and connection details must be known (host, base DN, etc.).
Getting the Configuration Right
Firstly, you will find the LDAP configuration in the Integrations section, under the Settings menu. In this page, you can define the connection information of your LDAP server and establish a connection with Easy!Appointments.
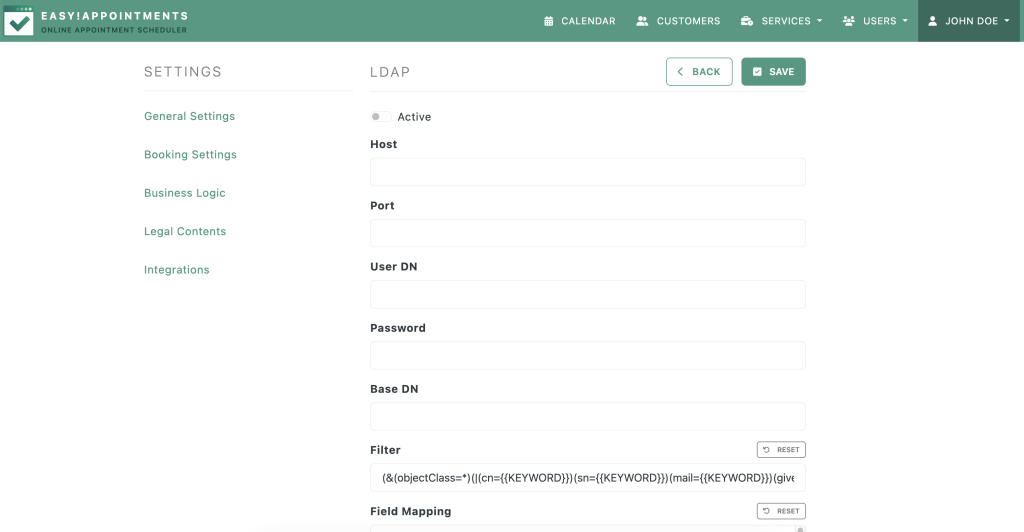
Moreover, once the connection is established, you can start searching and importing user accounts into Easy!Appointments, while assigning them a user role. These users will now be present in the app and can log in with their LDAP credentials.
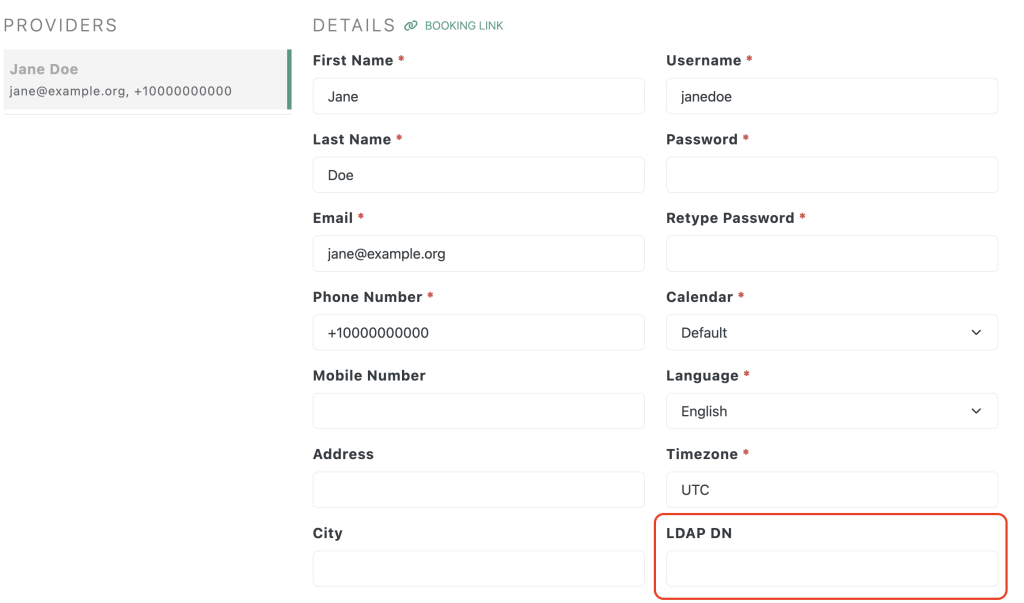
Alternatively, you can modify existing users and assign them the LDAP DN value, so that Easy!Appointments can find them during the login process.
Try the Login Page
After the connection is completed and the users are imported/matched, you will be able to use the login page with the LDAP credentials. The important part is that the username is matching the Easy!Appointments user, something that happens automatically if the user was imported through the LDAP configuration page.
Security Tips
- Use LDAPS (port 636) or StartTLS to encrypt credentials during transmission.
- Ensure only read-only service accounts are used for binding to LDAP.
- Rotate the bind account password regularly.